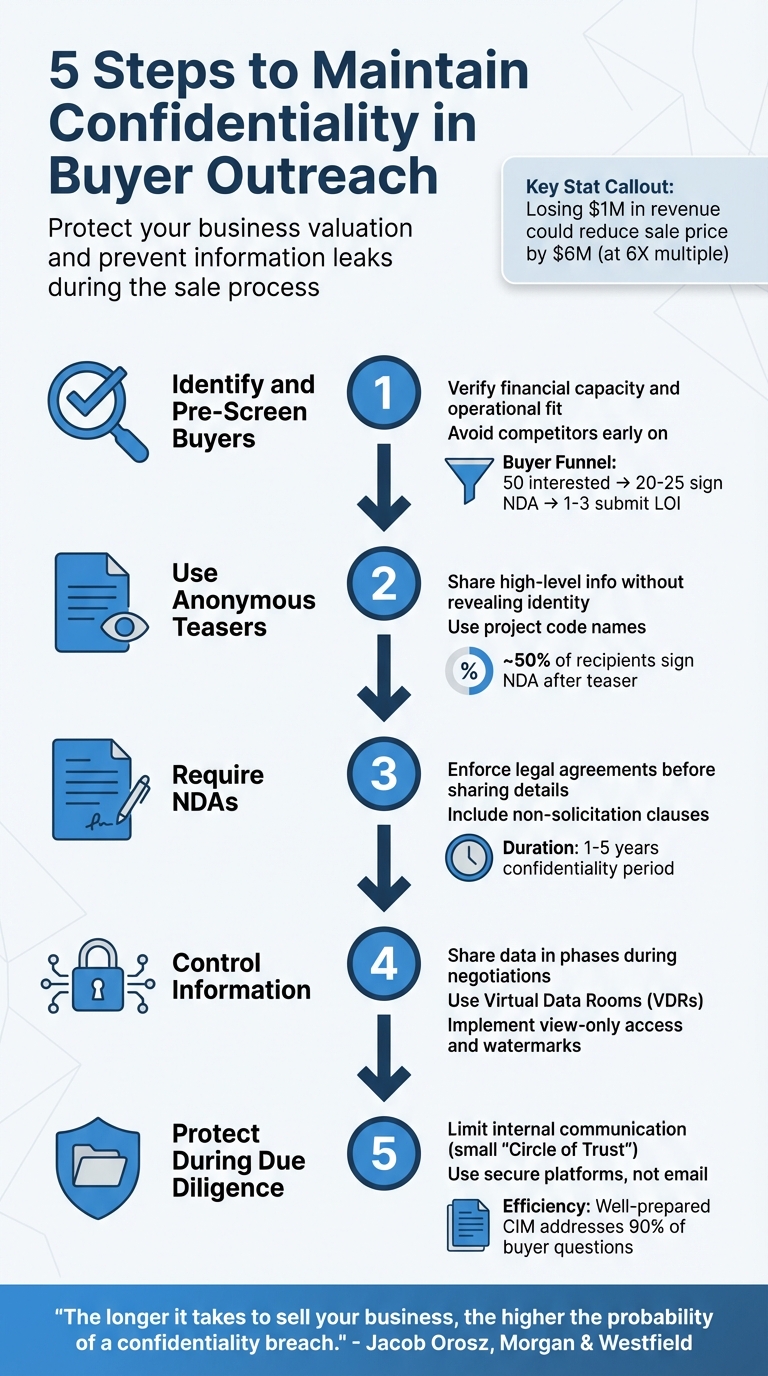
Maintaining confidentiality is critical when selling your business. A leak can lead to employee anxiety, loss of customer trust, or even a drop in valuation. For example, losing $1M in revenue for a business valued at a 6X multiple could reduce its sale price by $6M. Here’s how to protect sensitive information during buyer outreach:
- Identify and Pre-Screen Buyers: Verify financial capacity and operational fit before sharing details. Avoid competitors early on.
- Use Anonymous Teasers: Share high-level information without revealing your company’s identity to gauge buyer interest.
- Require NDAs: Enforce legal agreements to safeguard confidential data and prevent misuse.
- Control Information: Share data in phases, using tools like Virtual Data Rooms (VDRs) to manage access securely.
- Protect During Due Diligence: Limit internal communication and use secure platforms to share sensitive materials.
These steps ensure your business remains stable and valuable throughout the sale process.
5 Steps to Maintain Confidentiality When Selling Your Business
Selling Your Business? Don’t Share THIS Before the LOI
Step 1: Identify and Pre-Screen Buyers
Check buyer credibility before revealing any details about your business. A thorough pre-screening process ensures you focus on serious buyers while avoiding those who might waste your time or compromise your business.
Start by examining their financial capacity. Can they actually complete the purchase? Use tools like credit reports, background checks, or proof of funds to confirm their ability to close the deal. For individual buyers, third-party verification of funds is a smart move. Additionally, review their acquisition history and, if possible, seek input from previous CEOs they’ve worked with.
But it’s not just about money. Operational fit is equally important. Does the buyer have the experience and strategic vision to successfully run your business after the sale? This alignment can be a key factor in ensuring a smooth transition. In practice, the buyer funnel narrows significantly: for every 50 interested parties, only 20 to 25 typically sign an NDA and receive a Confidential Information Memorandum (CIM). Out of those, just 1 to 3 may submit Letters of Intent.
This careful vetting process not only saves time but also protects your sensitive business information.
Build a Qualified Buyer List
Once you’ve assessed buyer viability, organize them into categories based on risk levels. Direct competitors, for example, pose the greatest confidentiality risk. On the other hand, financial buyers – like private equity firms and investment groups – are generally lower risk and can be approached earlier. Buyers from related industries fall somewhere in the middle.
To protect your business identity during initial outreach, use a project code name instead of your actual company name. Additionally, assign unique identification numbers to every document you share. This allows you to trace the source of any potential information leaks. Keep the circle of people involved in the process small to further minimize risks.
Delay Competitor Outreach Until Later Stages
When it comes to competitors, timing is everything. Create a "Hold List" for direct competitors and hold off on contacting them until you’ve secured strong offers from other buyers. Delaying outreach to competitors ensures you protect sensitive information, including details about your employees and clients. Jacob Orosz, President of Morgan & Westfield, emphasizes:
"The longer it takes to sell your business, the higher the probability of a confidentiality breach."
Approaching competitors later also strengthens your negotiating position. With solid offers already on the table, you can engage competitors from a place of confidence, potentially driving up the final sale price. However, tread carefully – if a deal with a competitor falls through and sensitive information gets leaked, other buyers may lose interest, viewing your business as “tainted goods”.
Step 2: Use Anonymous Teasers to Generate Interest
After identifying qualified buyers, the next step is to capture their attention – without giving away your company’s identity. This is where an anonymous teaser, often called a "blind teaser", comes into play. Think of it as your business’s introduction, crafted to intrigue potential buyers while keeping your identity under wraps. Here’s how to create and share an effective teaser.
Keep it concise. For smaller businesses, aim for one to two pages; for larger ones, stick to five to ten pages. Use a high-level overview to showcase your business’s appeal, including broad geographic details (e.g., "Pacific Northwest" instead of a specific city) and financial ranges (e.g., "$4–$5 million" instead of "$4,250,000"). Avoid any specifics that could reveal your identity. As Ori Eldarov from OffDeal puts it:
"A confidential teaser initiates engagement while safeguarding your identity until buyers have proven they’re serious."
Make the teaser compelling. Highlight standout aspects like strong growth trends, recurring revenue, or a dominant position in a niche market. Mention potential growth opportunities, such as expanding into new regions or exploring untapped marketing channels. To ease concerns, include a simple, non-specific reason for the sale, such as "Owner retiring after 25 successful years in the industry."
Equally important is how you distribute the teaser. Use a blind email address (e.g., businessopportunity@securemail.com) or work with an M&A advisor to keep your company domain private. Assign a project code name, like "Project Bluebird", to all documents and communications. Before sending the teaser, call potential buyers to ensure they’re expecting it – this adds a personal touch and reinforces confidentiality.
Stick to the "No NDA, No Name" rule. The teaser is shared before an NDA is signed, but your company’s name and the full Confidential Information Memorandum (CIM) should only be disclosed after securing a signed NDA. Typically, about 50% of buyers who initially show interest will sign an NDA after reviewing the teaser, bringing you closer to a secure and confidential sale.
Step 3: Require NDAs and Qualify Buyers
Once you’ve confirmed buyer interest, the next step is to have potential buyers sign a Non-Disclosure Agreement (NDA). This document is essential for safeguarding your business from leaks, employee poaching, or competitors gaining access to sensitive information. Jacob Orosz from Morgan & Westfield highlights its importance:
"The NDA is the first document to be signed in a transaction and sets the tone for negotiations."
Not every interested party will make it to the stage of reviewing your financial details. These precautions help filter serious buyers from casual inquiries.
Drafting and Managing NDAs
A well-drafted NDA is key to protecting your business as you move forward in the sale process.
An effective NDA clearly defines what constitutes "confidential information." This can include financial records, customer lists, and intellectual property. It also restricts the buyer from using this information for anything other than evaluating the transaction. Additionally, the NDA should:
- Specify who can access the information, such as accountants or attorneys.
- Include a non-solicitation clause, which prevents buyers from hiring your employees or contacting your customers if the deal falls through.
- State how long the confidentiality obligations will last – typically between one and five years.
- Outline what happens if the deal doesn’t close, such as requiring all materials to be returned or destroyed.
Most NDAs used in mergers and acquisitions are unilateral, meaning only the buyer is bound by these terms. Sellers should avoid using a buyer’s standard NDA template and instead opt for a customized, seller-focused version to ensure stronger protection from the outset.
| NDA Component | Purpose in M&A |
|---|---|
| Definition of Confidential Info | Specifies what data (e.g., financials, IP) is protected. |
| Non-Solicitation Clause | Prevents buyers from recruiting employees or approaching customers. |
| Permitted Disclosures | Defines who (e.g., CPAs, attorneys) can access the information. |
| Return/Destruction Clause | Ensures data is returned or destroyed if the deal falls apart. |
| Term/Duration | Sets the confidentiality period, usually 1–5 years. |
Qualifying Buyers Before Sharing CIMs
After securing an NDA, the next step is to ensure the buyer is genuinely capable of completing the deal. Before sharing your Confidential Information Memorandum (CIM), take time to verify their financial and operational ability.
Ask questions about their acquisition experience, how many deals they’ve successfully closed, their decision-making process, and their funding sources. For individual buyers, consider requesting a credit report or conducting a background check to confirm their financial reliability. For corporate buyers, look into their acquisition history by speaking with executives from companies they’ve previously acquired.
If the potential buyer is a direct competitor, proceed with extra caution. Conduct additional due diligence before revealing sensitive information to avoid any risks.
A buyer’s willingness to invest time – whether through phone calls or in-person meetings – can be a strong indicator of their commitment. As always, safeguarding your sensitive data should remain a priority. Ensure that your CIM is shared only with buyers who have demonstrated their readiness to move forward.
For sellers seeking professional help in creating a detailed and secure CIM, Deal Memo offers on-demand, white-labeled CIM writing services designed specifically for M&A transactions.
sbb-itb-798d089
Step 4: Control Information During Negotiations
Following the buyer qualification process in Step 3, it’s critical to manage the flow of information as negotiations progress. This ensures confidentiality remains intact as discussions become more detailed and sensitive.
Manage the Indication of Interest (IOI) Phase
The IOI phase is when buyers submit preliminary offers based on the information you’ve shared so far. This is your opportunity to be strategic about what you disclose and to whom. Share information in stages, aligning with specific milestones. Hold back highly sensitive details until later in the due diligence process or after a definitive agreement is in place.
For example, redact or generalize sensitive data – like referring to top clients as “3 of the top 5 global e-commerce platforms” instead of naming them directly. For extremely confidential information, you might engage a neutral third-party firm to review the data and provide a summarized, anonymized report.
Leverage your Virtual Data Room (VDR) to maintain control. Use features like view-only access, restricted downloads, and time limits. Add dynamic watermarks for tracking and monitor VDR activity logs regularly to catch any unauthorized access.
Once preliminary offers are submitted, formalize confidentiality terms through the Letter of Intent (LOI).
Update Confidentiality Terms in the LOI
The LOI refines and expands the confidentiality terms initially covered by the NDA. It protects not only the data you’ve shared but also the sensitive details of the offer itself – such as pricing, deal structure, and even the existence of the negotiations.
Clearly outline which terms are binding – like confidentiality, exclusivity, and non-solicitation – and which are non-binding, such as the purchase price. As Morgan Lewis highlights:
"The most important item in any letter of intent is making sure that the description of which items are binding and which are not accurately matches the parties’ intent."
To maintain confidentiality, include survival clauses and require mutual agreement for public announcements. If the buyer is a direct competitor, implement "clean team" protocols. This ensures sensitive information is only accessible to third-party advisors or non-commercial employees, rather than the buyer’s operational team.
| Provision Type | Binding Status | Purpose |
|---|---|---|
| Confidentiality | Binding | Protects proprietary data and the existence of the deal |
| Exclusivity (No-Shop) | Binding | Prevents the seller from soliciting offers from other buyers |
| Non-Solicitation | Binding | Stops the buyer from poaching employees if the deal doesn’t proceed |
| Purchase Price | Non-Binding | Establishes a target value, subject to further due diligence |
| Governing Law | Binding | Defines which state’s laws will apply in case of disputes |
These legal protections should be paired with operational controls. Use tools like watermarking, VDR monitoring, and multi-factor authentication to ensure only authorized individuals have access to critical information.
Step 5: Protect Information During Due Diligence
During due diligence, maintaining strict confidentiality is just as important as legal safeguards. Once a Letter of Intent (LOI) is signed, the amount and sensitivity of shared information increase significantly. It’s crucial to control access to this information – both within your organization and on the buyer’s side.
Limit Internal Team Communication
Keep the circle of people aware of the sale as small as possible. This "Circle of Trust" should typically include the CEO, CFO, and a few key board members. Only involve additional stakeholders when absolutely necessary. To streamline communication, assign a dedicated team to handle all M&A-related discussions.
Make sure everyone involved understands the importance of discretion. Prepare a crisis-response plan that includes pre-written scripts for customers and talking points for suppliers, so you’re ready to act quickly if a leak happens. Meanwhile, leadership should focus on keeping day-to-day operations running smoothly to avoid drawing attention.
These internal precautions should be paired with strict external data-sharing protocols.
Use Secure Platforms for Data Sharing
Avoid using email to share sensitive documents. Instead, opt for Virtual Data Rooms (VDRs), which are widely recognized as the safest option for M&A due diligence. VDRs offer critical security features like controlled access, authentication, and real-time activity tracking.
Set document permissions carefully. For highly sensitive files, disable download and print options, making them available in view-only mode. Add user-specific watermarks to discourage unauthorized sharing and to trace the source of any leaks. Regularly review access logs to spot unusual activity. Screen capture prevention adds another layer of security.
For transactions involving competitors, consider using a "clean room" setup. In this arrangement, only a designated clean team – typically made up of third-party advisors or non-commercial personnel – can access competitively sensitive information. These team members should sign stricter confidentiality agreements to protect the data.
Additionally, redact sensitive details – such as customer names, detailed pricing, or employee compensation – until the buyer has demonstrated credibility and the deal is nearing completion. A well-prepared Confidential Information Memorandum (CIM) can address about 90% of buyer inquiries upfront, reducing the need to pull extra data from internal teams. If you need help creating a strong CIM, Deal Memo offers tailored, on-demand services. This minimizes risk and allows your team to stay focused on running the business.
Conclusion
Maintaining confidentiality during buyer outreach is critical – it protects your business’s valuation, keeps employees reassured, and preserves future opportunities. By following the five steps outlined in this guide, you can adopt a phased approach to disclosure, ensuring that sensitive information is shared only when absolutely necessary and at the right milestones.
This structured process not only protects your data but also fosters buyer confidence. Tools like anonymous teasers, NDAs, controlled negotiations, and secure data-sharing platforms allow you to stay in control of the deal’s narrative and timing. Such precautions help avoid disruptions caused by premature leaks, which can unsettle employees, customers, or even competitors. As Jacob Orosz, President of Morgan & Westfield, aptly puts it:
"Once the cat’s out of the bag about the sale of your business, it may be too late to control the narrative".
The risk of deal leaks is growing, and their consequences can be severe. In one instance, a single employee’s casual mention of acquisition plans to a supplier forced the seller to accelerate the deal timeline and implement urgent measures to address employee concerns. This highlights the importance of having strong confidentiality protocols in place.
Beyond preventing leaks, a well-organized disclosure process can boost buyer trust and create competitive tension – both essential for achieving a higher sale price. Buyers are more likely to view your business as well-managed and worth a premium when they see that you handle sensitive information with care. Combining legal safeguards like NDAs with operational controls, such as Virtual Data Rooms, sets the stage for a smooth and successful transaction.
Additionally, professional support during the due diligence phase, such as using services like Deal Memo for managing Confidential Information Memorandums (CIMs), can further enhance your confidentiality measures. A disciplined and secure approach to sharing information is not just a precaution – it’s a cornerstone for maximizing the outcome of your sale.
FAQs
What are the potential risks of not keeping buyer outreach confidential?
Failing to keep information under wraps during buyer outreach in an M&A transaction can have serious consequences for both the deal and the business. For starters, employee morale often takes a hit if staff catch wind of a potential sale. This can lead to disengagement or even resignations, disrupting day-to-day operations and potentially cutting into earnings – which, in turn, might lower the company’s valuation. On top of that, customers who hear rumors may pull back on orders or turn to competitors, directly affecting revenue and the eventual purchase price. And let’s not forget about competitors – they can seize the opportunity to poach clients or slash prices, further straining cash flow and tarnishing market perception.
Beyond these operational risks, breaches of confidentiality can also lead to legal and financial headaches. For example, leaking sensitive details could violate non-disclosure agreements, stall the transaction, or even cause the deal to collapse entirely. The fallout? Wasted time, higher costs, and a weakened negotiating position for the seller. These setbacks often translate into a reduced purchase price or the loss of potential buyers. Bottom line: safeguarding confidentiality is essential to protecting valuation, keeping stakeholders on board, and ensuring the transaction moves forward without unnecessary hurdles.
How can I verify a buyer’s financial ability before sharing sensitive information?
Before handing over a Confidential Information Memorandum (CIM) or any other sensitive details, it’s crucial to verify the buyer’s financial capacity. Ask for proof of funds – this could include recent bank statements, a certified source-of-funds letter, a financing commitment from a lender, or a balance sheet showing enough liquid assets to cover the purchase price. These documents confirm the buyer’s ability to move forward with the transaction.
Incorporate this financial check into your pre-screening process. Start by having the buyer sign a non-disclosure agreement (NDA) to protect your information. After that, request proof of financial capacity before granting access to the CIM. If the buyer can’t provide adequate documentation, you can withhold further details, protecting confidentiality and steering clear of unnecessary discussions with unqualified prospects.
This two-step process – combining an NDA with financial verification – creates an extra layer of security, ensuring that only serious, financially capable buyers access sensitive information.
How do Virtual Data Rooms (VDRs) help protect sensitive information during a business sale?
Virtual Data Rooms (VDRs) offer a safe, centralized space for managing and sharing sensitive documents during a business sale. Instead of relying on email, which can be vulnerable to hacking or accidental leaks, VDRs provide an encrypted environment to keep information secure.
With granular permissions, sellers can decide who sees what – whether that’s view-only access or time-limited permissions. Detailed audit logs keep track of user activity, making it easier to spot any unauthorized actions. Additional tools like watermarking, version control, and secure Q&A modules add extra layers of protection, ensuring sensitive information stays secure throughout the due diligence process.